Remediate User Enumeration in Drupal

Introduction
User enumeration is a critical vulnerability that can compromise the security of Drupal websites. In simple terms, it allows malicious actors to extract valid usernames through various techniques, posing a significant threat to user privacy and data integrity. This blog will focus on exploring effective remediation techniques specifically tailored for Drupal to address the issue of user enumeration.
Throughout this article, you will gain insights into:
- Understanding the concept of user enumeration and its implications for website security.
- Identifying vulnerabilities prone to user enumeration in Drupal.
- Implementing comprehensive security measures for user authentication.
- Detecting and mitigating brute-force attacks effectively.
By the end of this blog, you will be equipped with practical strategies to fortify your Drupal website against user enumeration and bolster its overall security posture.
Understanding User Enumeration in Drupal
User enumeration is a critical security vulnerability that can have severe consequences for the overall security of a Drupal website. In this section, we will delve into the definition of user enumeration within the context of Drupal, discuss the utilization of brute-force attacks, and explore effective measures to prevent such enumeration attacks.
Definition of User Enumeration
In the context of web application security, user enumeration refers to the process of identifying valid usernames or user accounts through systematic trial and error. Attackers exploit this vulnerability by attempting to enumerate usernames using various techniques, such as brute-force attacks. By enumerating valid usernames, attackers gain valuable information that can be used to launch further attacks, such as credential stuffing or targeted phishing campaigns.
Brute-Force Attacks for User Enumeration
Brute-force attacks are commonly employed for user enumeration purposes. These attacks involve systematically trying all possible combinations of usernames and passwords until a valid username is identified. Since Drupal websites often have a default login page accessible to anyone, attackers can easily automate these brute-force attempts using specialized tools or scripts.
Impact on Drupal Site Security
The impact of user enumeration on the overall security posture of a Drupal site cannot be underestimated. By successfully enumerating valid usernames, attackers gain valuable insights into the site's user base and can focus their efforts on compromising specific accounts or targeting privileged users. This can lead to unauthorized access, data breaches, and other malicious activities that can severely undermine the confidentiality, integrity, and availability of the website.
To protect against user enumeration in Drupal, it is crucial to implement robust remediation techniques that address vulnerabilities prone to this attack vector. In our subsequent discussions, we will explore these techniques in detail to help you strengthen your Drupal site's security and safeguard against user enumeration threats.
Identifying Vulnerabilities Prone to User Enumeration
To effectively fix user enumeration in Drupal, you need to first find out the vulnerabilities that can make a website prone to this type of attack. When you understand these weaknesses, website owners and administrators can take proactive measures to mitigate the risks and enhance the security of their Drupal sites. Here are some common areas of weakness in Drupal websites that can be exploited for user enumeration:
1. Insecure Login Forms
Insecure login forms can provide valuable information to attackers attempting user enumeration. For example, if an error message is displayed when an incorrect username is entered, it indicates that the username exists in the system. Similarly, if the login form responds differently for valid and invalid usernames (e.g., a delay in response time), it can be used to determine whether a username is valid or not.
2. Password Recovery Mechanisms
Password recovery mechanisms, such as the "Forgot Password" page, can also be vulnerable to user enumeration. If an attacker can determine whether a specific email address or username exists in the system by observing the response from the password recovery feature, they can use this information to launch targeted attacks.
3. Brute-Force Attacks
Brute-force attacks involve systematically trying different combinations of usernames and passwords until a valid combination is found. These attacks can be facilitated by vulnerabilities in Drupal websites, such as weak password policies or lack of account lockout mechanisms. By exploiting these weaknesses, attackers can easily enumerate user accounts and gain unauthorized access.
Understanding these vulnerabilities is essential for implementing effective remediation techniques. By addressing these weaknesses through secure coding practices and implementing appropriate security measures, website owners can significantly reduce the risk of user enumeration in their Drupal sites.
1. Server Response and Error Messages
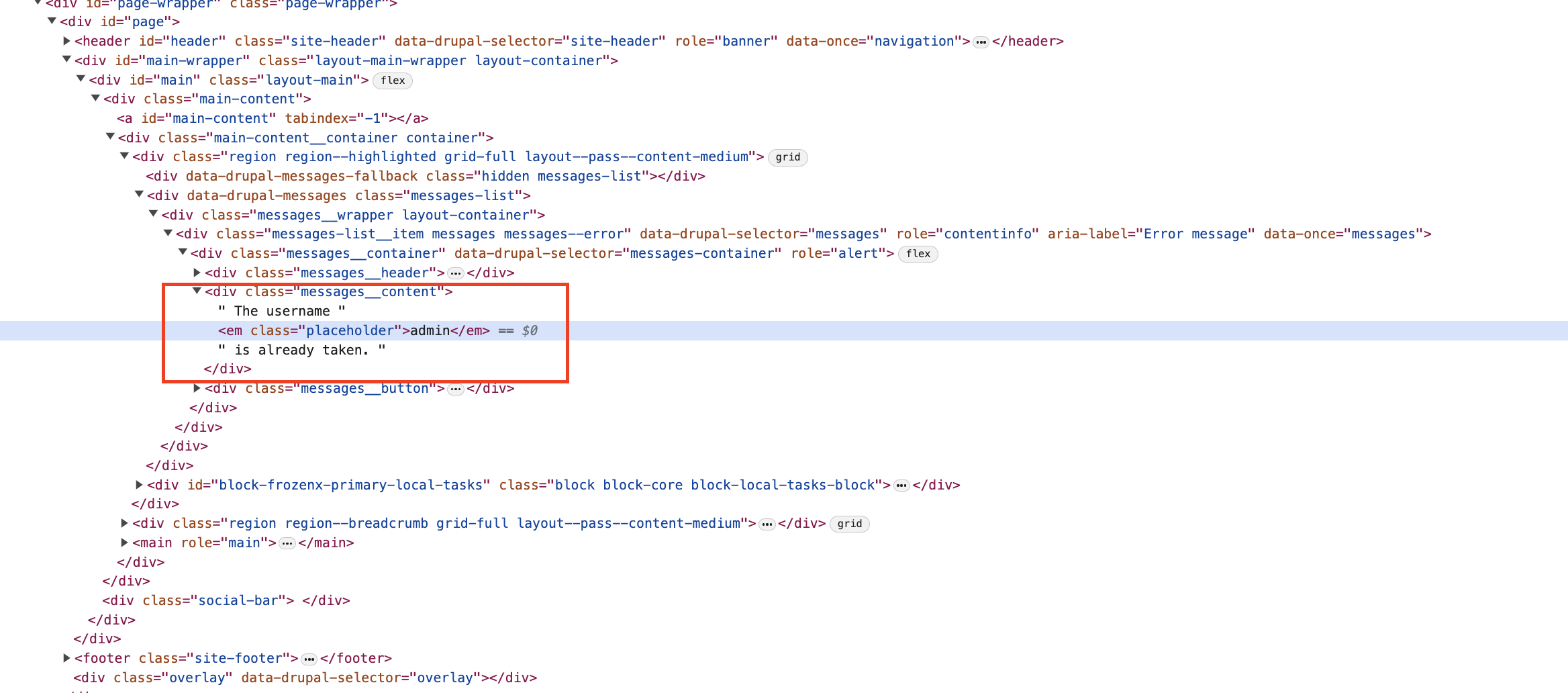
When it comes to fixing user enumeration in Drupal, using the right server responses and error messages can be an effective way to start. But be careful: some generic error responses can accidentally reveal valid usernames in Drupal, making user enumeration more likely.
Real-life examples like Outlook Web Access (OWA) and Metasploit have shown how user enumeration can be done by analyzing server responses. In these cases, by looking at the error messages they got when trying to log in, attackers could figure out if a username was valid or not on the Drupal site they were targeting.
To lower this risk, it's important to have secure ways of dealing with errors. Here are some suggestions:
- Customize Error Messages: Avoid using generic error messages that give away too much about what went wrong. Instead, use more general messages that don't reveal any sensitive details.
- Implement Rate Limiting: Put limits on how many times someone can try to log in within a certain time period. This can help stop automated brute-force attacks and make it harder for attackers to do user enumeration.
- Use Consistent Error Responses: Make sure the error messages are the same whether the username or password is wrong. That way, you won't be giving potential attackers any clues about which usernames are valid.
- Monitor and Analyze Logs: Keep an eye on your server logs regularly so you can spot any strange activity or patterns related to user enumeration. Looking through these logs can help you find and deal with security issues faster.
By following these suggestions for secure error handling, you can greatly reduce the chance of user enumeration happening because of server responses and error messages in Drupal.
Remember, fixing user enumeration is just one part of keeping your website secure. In the next sections, we'll look at more ways to make sure users are who they say they are when logging in to Drupal sites.
2. Two-Factor Authentication (2FA)
Two-factor authentication (2FA) is an extra security measure that can be used to strengthen user authentication and prevent enumeration attacks. In the context of Drupal websites, implementing strong 2FA methods adds an additional layer of protection to the login process, making it harder for hackers to gain unauthorized access.
How Does Two-Factor Authentication Work?
- The user enters their username and password as usual.
- Instead of immediately gaining access, the user is prompted to provide a second form of verification.
- This second factor can be something the user knows (like a PIN), something they have (like a physical token), or something unique to them (like their fingerprint).
- Once the second factor is successfully verified, only then will the user be granted access to their account.
Why Is Two-Factor Authentication Important?
Two-factor authentication provides an extra layer of security because it requires attackers to have both the user's password and access to their second factor device or method. Even if a hacker manages to steal or guess a user's password, they would still need this additional piece of information to gain entry.
Benefits of Two-Factor Authentication
Implementing robust 2FA methods in Drupal websites offers several advantages:
- Increased Security: By adding an extra layer of verification, it becomes significantly more difficult for unauthorized individuals to access user accounts.
- Protection Against Password Guessing: If someone tries to guess a user's password, they won't be able to log in without the second factor.
- Mitigation of Credential Stuffing Attacks: With 2FA in place, even if hackers obtain login credentials from one source (e.g., a data breach on another website), they won't be able to use those credentials alone to access accounts on your Drupal site.
- Enhanced User Trust: By implementing strong security measures like 2FA, you demonstrate your commitment to protecting user data and can increase trust among your audience.
Common Two-Factor Authentication Methods
Here are some of the most commonly used second factors in 2FA implementations:
- SMS Tokens: A unique code is sent to the user's mobile device via SMS, which they must enter during the login process to verify their identity.
- Authentication Apps: Users install an authentication app (such as Google Authenticator or Authy) on their mobile device, which generates time-based one-time passwords (TOTPs) for verification.
- Email Verification: A verification link or code is sent to the user's registered email address, which they must click or enter during login.
- Physical Security Keys: Users are provided with a physical USB or NFC key that they need to insert or tap for authentication.
- Biometric Verification: This includes using fingerprints, facial recognition, or other unique biological characteristics to verify identity.
Important Considerations for Two-Factor Authentication
While two-factor authentication offers significant benefits, it's essential to consider the following factors when implementing it:
- User Experience: Striking a balance between security and usability is crucial. Ensure that the chosen 2FA method(s) are convenient for your users without compromising security.
- Backup Options: Provide alternative methods for users who may not have access to their primary second factor device (e.g., a lost phone) or encounter issues receiving verification codes.
- Security Risks of SMS Tokens: While widely used and convenient, relying solely on SMS as a second factor introduces the risk of SIM swap attacks, where an attacker fraudulently activates a new SIM card with the target's phone number.
- Emerging Technologies: Stay informed about new developments in two-factor authentication and consider adopting more advanced methods as they become available.
Implementing robust 2FA mechanisms in Drupal websites enhances overall user authentication security and contributes to a more resilient defense against user enumeration attempts.
3. Web Application Firewall (WAF)
A web application firewall (WAF) adds an extra layer of protection against user enumeration and other malicious activities. It works by monitoring and filtering incoming traffic to identify and block suspicious enumeration attempts before they reach your Drupal site.
Key Benefits of Using a WAF for Drupal Security
Here are some key benefits of using a web application firewall (WAF) for securing your Drupal website:
1. Continuous Monitoring and Filtering
WAFs continuously monitor incoming traffic to identify patterns that may indicate enumeration attempts. They can filter out malicious requests, blocking them before they reach your Drupal site.
2. Rate Limiting for Login Requests
WAFs can enforce rate limits on login requests, preventing an excessive number of login attempts within a specific period. This effectively reduces the risk of brute-force attacks and user enumeration.
3. Checking IP Reputation
WAFs can check the reputation of IP addresses attempting to access your site. If an IP address is associated with suspicious activities or has a history of malicious behavior, the WAF can block or challenge those requests.
4. Behavioral Analysis with Machine Learning
Advanced WAF solutions utilize machine learning algorithms to analyze user behavior and detect anomalous patterns. This helps identify potential enumeration attempts based on deviations from normal login activity.
5. Integration with Security Intelligence
Some WAFs incorporate threat intelligence feeds, which provide real-time information about known malicious IPs or patterns. This enables proactive blocking of enumeration attempts based on up-to-date threat data.
By implementing a web application firewall for Drupal, you add an extra layer of protection against user enumeration and other security threats. It complements other remediation techniques discussed earlier, such as two-factor authentication (2FA) and secure error handling practices. Together, these measures strengthen the security posture of your Drupal website and help safeguard user accounts from unauthorized access.
Note: While a WAF is a valuable tool in your security arsenal, it should not be the sole defense mechanism. It is crucial to implement comprehensive security measures, including secure user authentication practices and detection mechanisms for brute-force attacks, to ensure the overall security of your Drupal site.
Implementing Comprehensive Security Measures for User Authentication
When it comes to fixing user enumeration in Drupal, it's important to do more than just address the enumeration itself. Implementing comprehensive security measures for user authentication can greatly strengthen the overall security of your Drupal website. Here are some best practices to consider:
- Validate User Inputs: One of the key steps in preventing malicious account enumeration is to validate user inputs during the registration process. By implementing strong input validation mechanisms, you can ensure that only legitimate and properly formatted user data is accepted. This helps to prevent attackers from exploiting vulnerabilities by submitting malformed or malicious data.
- Enforce Strong Password Policies: Passwords are often the weakest link in user authentication. By enforcing strong password policies, such as requiring a minimum length, a combination of uppercase and lowercase letters, numbers, and special characters, you can enhance credential protection. Additionally, consider implementing password expiration and complexity requirements to further strengthen security.
- Leverage Secure Hashing Algorithms: Storing passwords securely is crucial in preventing unauthorized access to user accounts. Instead of storing passwords in plain text or using weak encryption methods, it is recommended to leverage secure hashing algorithms like bcrypt or Argon2. These algorithms are designed to be computationally expensive, making it difficult for attackers to crack hashed passwords even if they gain access to the stored hashes.
By following these best practices for user authentication, you can significantly reduce the risk of user enumeration and enhance the overall security of your Drupal website.
Detecting and Mitigating Brute-Force Attacks
Brute-force attacks are a common method used by attackers to gain unauthorized access to user accounts. In the context of user enumeration in Drupal, it is crucial to implement effective strategies to detect and mitigate these types of attacks. Here are some key points to consider:
1. Response Time Difference Detection
By utilizing server-side monitoring techniques, abnormal variations in login request processing times can be identified. Attackers often employ automated tools that generate a high volume of login requests within a short period. Monitoring the response times can help detect such brute-force attempts.
2. Leveraging Username and Password Validation Mechanisms
Implementing username and password validation mechanisms can help detect and disrupt automated brute-force attempts. For example, if multiple failed login attempts are made using the same username but different passwords within a specific time frame, it could indicate a brute-force attack in progress.
3. Implementing Account Lockout Policies
To limit the impact of successive failed login attempts, implementing account lockout policies is an effective measure. After a certain number of failed login attempts, user accounts can be temporarily locked or disabled for a specified period. This prevents attackers from continuously guessing passwords.
4. Using CAPTCHA Challenges
Differentiating between human users and bots is essential in mitigating brute-force attacks. CAPTCHA challenges can be implemented during the login process to ensure that only legitimate users can proceed further. CAPTCHA requires users to perform an action (such as solving a puzzle or entering characters from an image) that is difficult for automated tools to complete.
By incorporating these detection and mitigation strategies, the risk of brute-force attacks and subsequent user enumeration can be significantly reduced in Drupal websites.
Remember: "Prevention is better than cure." It is essential to proactively implement security measures rather than waiting for an attack to occur.
Conclusion
Addressing user enumeration in Drupal is a critical step towards enhancing the security posture of your website. By implementing the remediation strategies discussed in this article, you can significantly reduce the risk of unauthorized access and potential data breaches. Remember that safeguarding your Drupal site requires continuous attention and adaptation to emerging threats. Stay vigilant, prioritize robust authentication mechanisms, and remain proactive in fortifying your defenses against evolving security challenges. With these measures in place, you can effectively mitigate the risks associated with user enumeration and contribute to a safer online environment for your users.